You have a password or some secret in your Git repository, and you want to remove it. I recently had the same problem in one of my repositories. I will show you a convenient and simple way to get rid of any accidentally committed secret in your Git repository.
Understanding the Situation
First of all, we need to make sure we have a common understanding of the problem. We committed a secret into a Git repository. It is a problem because everyone with access to our source code has access to secret information. We don’t want any secrets in our source code repositories.
It doesn’t matter if we remove the secret with another commit or remove the file from the repository. The secret will always remain in the Git history.
If we want to get rid of the secret, we need to rewrite the Git history. It can be challenging, especially for developers like me, who usually only use basic Git commands.
I have an example repository that contains secrets in a config file that I want to remove. Let’s take a look at the file.
{
"mailPassword": "&T95HgN~vRs>{Wv§ZsAateQ$mKX8@aat",
"jwtSecret": ":vb5#jSKKy<fQxtD+.b_3u9syteEB8_f7@c7k6Ct3%_v7z>g&Sx)2s>nRZMXnUf$"
}
I made multiple commits on this file. That’s why the secret will remain in the Git history, even when I remove it in a future commit.
Possible Solutions
While there are native Git commands like git filter-branch that we can use to rewrite the Git history, it still is somewhat error-prone. It is especially true if you haven’t used those commands before.
I can only speak for myself, but I prefer using a dedicated tool that supports me in doing the right thing. Luckily, I came across BFG Repo Cleaner.
The BFG Repo Cleaner
BFG Repo Cleaner is a Java tool, which means that you need to have the Java runtime installed on your computer and that Java needs to be available from the command line.
BFG Repo Cleaner offers a simpler, faster alternative to git-filter-branch to remove secret data from your Git repository history.
Download the tool and move it to a location that you can easily access from the command line. I moved it into the root of the C:\ drive on my Windows computer.
Preparing the Repository
We need to make sure that our repository is in a clean state. I suggest that you don’t have any pending changes, and you pull the latest changes from remote repositories to make sure you work on the latest version of your code.
Also, we need to make sure that we remove all secrets from the repository with another commit before we use the BFG Repo Cleaner. Let’s open the config file and remove the secrets and commit the changes.
Creating the Password.Txt File
Next, we create a new file in the root folder of the repository and name it password.txt. In this file, we insert secrets that we want to remove from the repository. Make sure that you put every secret on a new line.
&T95HgN~vRs>{Wv§ZsAateQ$mKX8@aat
:vb5#jSKKy<fQxtD+.b_3u9syteEB8_f7@c7k6Ct3%_v7z>g&Sx)2s>nRZMXnUf$
Running BFG Repo Cleaner
Next, we open a command-line tool and navigate to the root of the repository. We run the following command to run the BFG Repo Cleaner.
java -jar C:\bfg-1.14.0.jar --replace-text password.txt
Depending on your repository’s size and the number of commits, the tool will take a few seconds or a few minutes to complete.
Checking the Repository
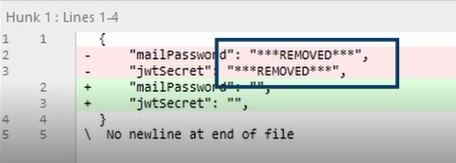
Now, let’s take a look at the Git history of the repository. As you can see, the tool replaced the secrets with a generic string.
Pushing Your Rewritten Repository
If you are working with remotes, for example, GitHub, you need to force push the changes using the following command:
git push --force origin main
Origin is the name of the remote, and main is the name of the branch.
You need to do that because the history rewrite made every commit hash change starting with the first commit that contained any of your secrets.
Dealing with Exposed Secrets
Also, make sure that all copies of your repository, including all remotes, are cloned again. Otherwise, you won’t be able to push changes because the history of the two Git repositories doesn’t match.
But what about the exposed secrets?
As long as you are the only person with access to the repository, you are good to go. In case the repository was pushed to another location, for example, GitHub, we need to assume that there is at least another copy of your repository and, therefore, your secrets aren’t secret anymore, and you should change any passwords or other secret information that was exposed.